Disabling Windows Defender (now called Microsoft Defender Antivirus) may be necessary for developers, software testers, or IT professionals. Deactivation allows for testing applications without interference or for installing a third-party antivirus solution.
Important: Disabling Defender leaves a system unprotected. Always re-enable security features after testing to protect against viruses and malware.
When Should You Disable Defender?
- To test potentially malicious software for security research
- When running programs that Defender falsely detects as threats
- Before installing another antivirus for conflict prevention
- To avoid real-time scans during performance-sensitive tasks
How to Temporarily Turn Off Windows Defender
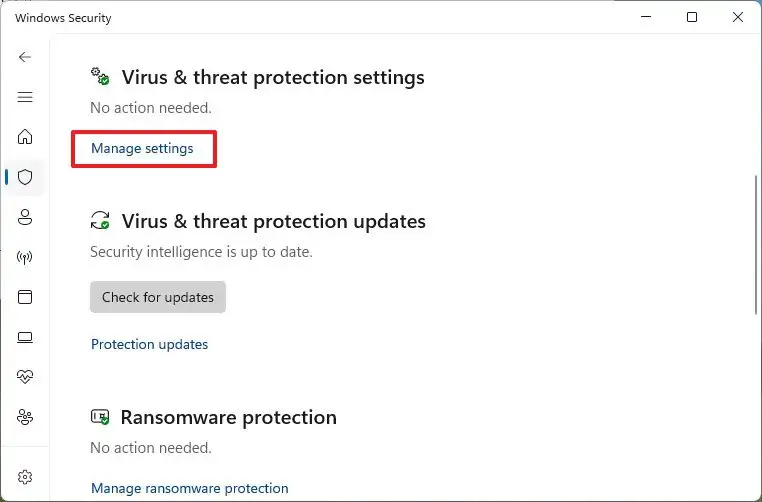
- Open Windows Security.
- Go to Virus & threat protection settings.
- Toggle off Real-time protection.
This only disables Defender until the next reboot.
How to Permanently Disable Windows Defender with PowerShell
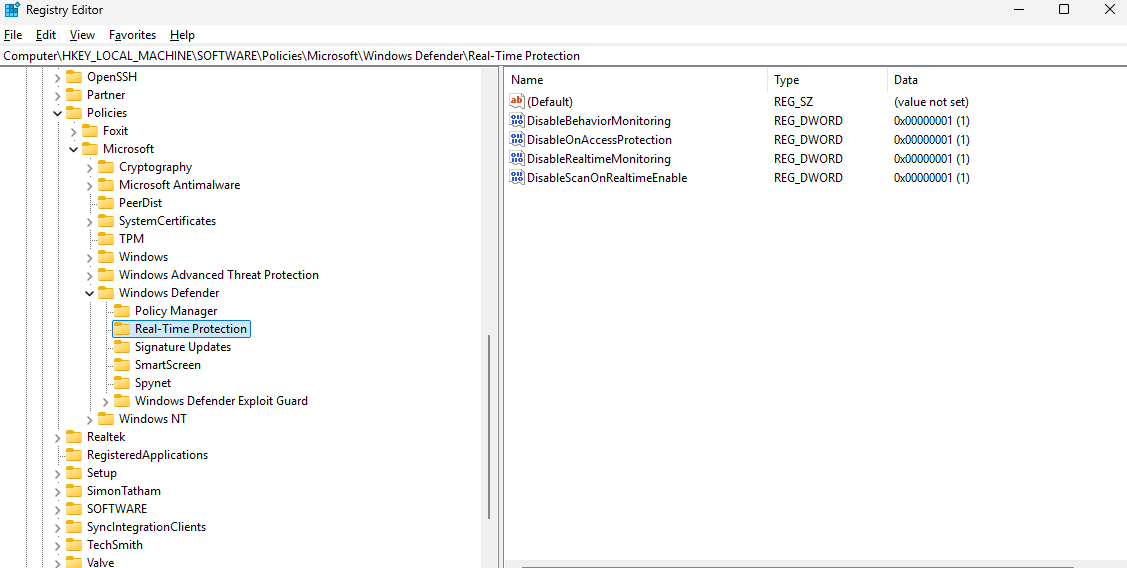
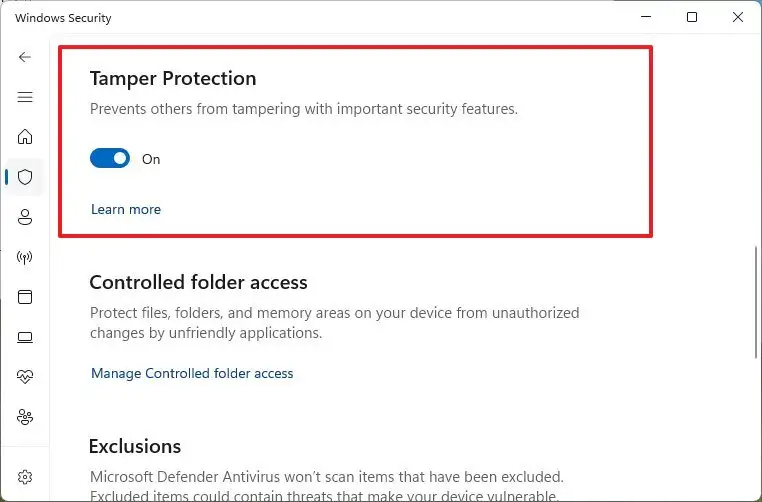
For a permanent solution, advanced users can use a PowerShell script to update system registry keys. Tamper Protection must be disabled manually in Windows Security before running the script. You will need Administrator rights.
PowerShell Script
# PowerShell script to permanently disable Microsoft Defender Antivirus on Windows 11
# Must be run as Administrator
# Before running, disable Tamper Protection manually from Windows Security settings
# Base registry path
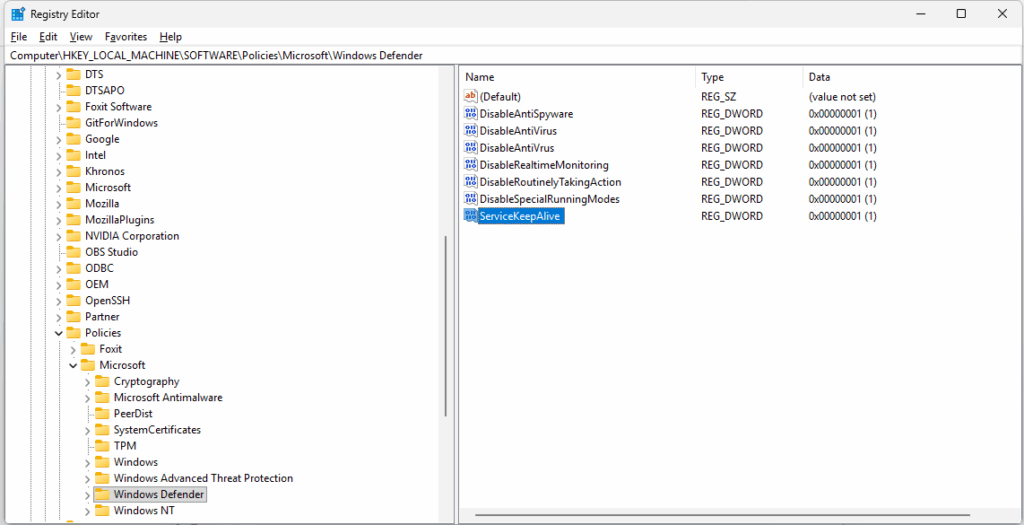
$regPath = "HKLM:\SOFTWARE\Policies\Microsoft\Windows Defender"
# Create Windows Defender key if it doesn't exist
If (-Not (Test-Path $regPath)) {
New-Item -Path "HKLM:\SOFTWARE\Policies\Microsoft" -Name "Windows Defender" | Out-Null
}
# Set DWORD values to disable Defender core features
New-ItemProperty -Path $regPath -Name "DisableAntiSpyware" -PropertyType DWord -Value 1 -Force
New-ItemProperty -Path $regPath -Name "DisableRealtimeMonitoring" -PropertyType DWord -Value 1 -Force
New-ItemProperty -Path $regPath -Name "DisableAntiVirus" -PropertyType DWord -Value 1 -Force
New-ItemProperty -Path $regPath -Name "DisableSpecialRunningModes" -PropertyType DWord -Value 1 -Force
New-ItemProperty -Path $regPath -Name "DisableRoutinelyTakingAction" -PropertyType DWord -Value 1 -Force
New-ItemProperty -Path $regPath -Name "ServiceKeepAlive" -PropertyType DWord -Value 0 -Force
# Real-Time Protection subkey and its DWORD values
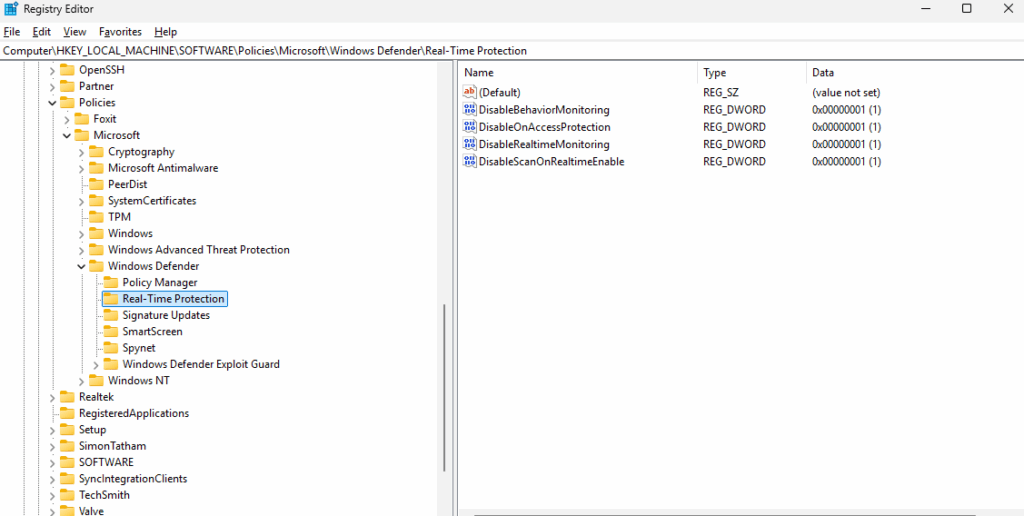
$rtpPath = "$regPath\Real-Time Protection"
If (-Not (Test-Path $rtpPath)) {
New-Item -Path $regPath -Name "Real-Time Protection" | Out-Null
}
New-ItemProperty -Path $rtpPath -Name "DisableBehaviorMonitoring" -PropertyType DWord -Value 1 -Force
New-ItemProperty -Path $rtpPath -Name "DisableOnAccessProtection" -PropertyType DWord -Value 1 -Force
New-ItemProperty -Path $rtpPath -Name "DisableScanOnRealtimeEnable" -PropertyType DWord -Value 1 -Force
New-ItemProperty -Path $rtpPath -Name "DisableRealtimeMonitoring" -PropertyType DWord -Value 1 -Force
# Signature Updates subkey and its DWORD value
$sigPath = "$regPath\Signature Updates"
If (-Not (Test-Path $sigPath)) {
New-Item -Path $regPath -Name "Signature Updates" | Out-Null
}
New-ItemProperty -Path $sigPath -Name "ForceUpdateFromMU" -PropertyType DWord -Value 1 -Force
# Spynet subkey and DWORD value
$spynetPath = "$regPath\Spynet"
If (-Not (Test-Path $spynetPath)) {
New-Item -Path $regPath -Name "Spynet" | Out-Null
}
New-ItemProperty -Path $spynetPath -Name "DisableBlockAtFirstSeen" -PropertyType DWord -Value 1 -Force
Write-Host "Registry changes made to disable Microsoft Defender Antivirus permanently."
Write-Host "Please restart your computer for the changes to take effect."
What Does the Script Do?
- Creates necessary registry keys to store settings if they don’t already exist
- Disables real-time protection, antispyware, antivirus, and several automated actions
- Disables background monitoring and active scanning features
- Blocks signature updates and cloud-based protection features
- Requires a system restart to fully apply changes
Explanation of the Script
- The script operates by modifying Windows registry keys under the path
HKLM:\SOFTWARE\Policies\Microsoft\Windows Defenderand its subkeys. - It sets various
DWORDvalues to1to disable core antivirus features such as real-time monitoring, behavior monitoring, and automatic actions. - It creates registry keys if they do not already exist to ensure changes take effect.
- The script disables signature updates and some intelligent security features like Spynet.
- Important note: Tamper Protection in Windows Security must be disabled manually before running this script, as it prevents registry modifications related to Defender.
- The script requires Administrator privileges and a system restart for changes to apply.
- This method disables Defender permanently until reverted, useful in scenarios like testing or using alternative security solutions.
Safety and Testing Reminder
Disabling Microsoft Defender with this script is best reserved for controlled environments (like test labs or VMs). Do not disable essential security features on devices in daily use.